Unit 5 Notes
Unit 5 Notes
5.1 Beneficial and Harmful Effects
- Come up with three of your own Beneficial and corresponding Harmful Effects of Computing
| Beneficial Effects | Harmful Effects |
|---|---|
|
|
- Talk about dopamine issues above. Real? Parent conspiracy? Anything that is impacting your personal study and success in High School? Sometimes when i’m on my computer, I lose track of time and end up spending my entire day on my computer. This can be both good and bad. Far starters, it has a negative impact because I don’t spend any time with my family or socializing with people in person. Since a computer allows me to do everything online including communicating with others, it creates a lazy mindset that makes me less social and outgoing. However, computers are also a crucial and beneficial part of my life because it allows me organize and complete my school work. In addition, my computer gives me access to the internet which provides me with millions of resources that are just a click away.
5.2 Digital Divide
-
Think of three beneficial effects of your projects based on 5.1 Unit
- Our project can help people make an informed decision about what type of car they are looking to buy. Users can gain specific information on the type, model, mileage, and price of a car.
- Our project can help people save time when buying a car. Instead of having to spend hours going from car dealer to car dealer asking questions about a car, the user can find all the information they need in one place on one website.
- Since our project has a sign up and log in feature, this means that users can “save” cars their account and refer beck to them by logging in to the website again. This feature makes looking for information easy and fast.
-
Think of a potential harmful effect of your project.
- I think that our website could potentially be a disruptor in how people look for a car to buy. Instead of seeing the car in person, the user might base their purchase only on what they see online but when they actually get the car, it isn’t what they were anticipating. This can create some false expectations which wouldn’t be good for someone trying to make an important purchase.
-
What concerns do you have personally about the digital divide? For yourself or for others.
- Its obviously very upsetting that digital divide is something that exists. I think its very unfair that not everyone has access to the same opportunities and education, something that is partially effected by the digital divide. Those who do not have computers lose access to the internet and all the information that comes with it. As a result, they fall behind other, not because they lack the skill, but because they lack the resources which is extremely unfair.
- Answer with an opinion and learnings so far this year: What are pros/cons on internet blockers at router and lack of admin password on lab machines at school?
| Pros | Cons |
|---|---|
|
|
5.3 Computer Bias
Google “What age groups use Facebook” vs “… TikTok”? What does the data say? Is there purposeful exclusion in these platforms? Is it harmful? Should it be corrected? Is it good business?
- The age group that uses Facebook are people ages 25-34
- The age group uses tik tok are people ages 10-19
- there are purposeful exclusions on platforms like tik tok. For example, people who are 13 and under can’t sign up and tik tok does this to prevent young children from viewing possibly inappropriate content so it’s beneficial in that sense so it shouldn’t be corrected. It’s bad business for a company like Facebook which is primarily a platform for older people. Facebook thus loses younger users.
Why do virtual assistants have female voices? Amazon, Alexa Google, Apple Siri. Was this purposeful? Is it harmful? Should it be corrected? Is it good business?
- using only female voices might imply to some that females fill the role of “submissiveness” as they serve the owner of the virtuous devices. It might also promote the bias that women are assistants.
- this should be corrected and virtual assistants should include more male voices to make things more balanced
- it’s good business because people might find female voices more pleasing and thus be more inclined to buy the device so in that sense, it’s very purposeful that these companies choose to set the voice to female by default.
Talk about an algorithm that influences your decisions, think about these companies (ie FAANG - Facebook, Amazon, Apple,Netflix, Google)
- there are algorithms that different companies use to capture the users attention. For example, tik tok has a “for you page” which shows videos that appeal to the users interests and these interests are filled out beforehand by the user. In addition this algorithm pushes trends to the user which can have harmful effects such as in the case of the “devious lick” trend. In addition companies like Facebook and Amazon have ads on the side of your screen based on your search history.
Does the owner of the computer think this was intentional? If yes or no, justify you conclusion.
- I don’t think the owner thinks its intentional because he’s carrying a light joking tone throughout the video showing how he’s more so making fun of the machine vs being angry at it.
How do you think this happened?
- the lightning might have been bad or during development, the developers may have only tested the technology with white testers thus failed to recognize the errors when a black man tested the tech
Is this harmful? Was it intended to be harmful or exclude?
- this is harmful because it’s unintentionally exclusive
Should it be corrected? What would you or should you do to produce a better outcome?
- this should be corrected and developers definitely need to solve the tech to make it inclusive of people with all skin colors. I think the company needs to do more testing.
Write summary/thoughts/conclusions from each of the exercises above. Focus on avoiding Bias in algorithms or code you write.
- Every product that is developed will have some type of bias. The best way to combat this bias is to get feedback and opinions from a diverse group of people. That way, any software can have an inclusive usage and be good for everyone
5.4 Crowd Sourcing
We have all experienced Crowdsourcing by using external data through API’s, namely RapidAPI. This data has influenced how we code and shown possibilities in obtaining and analyzing data. Discuss APIs you have used.
- I have used an API with symptoms including cough, fever, etc. I used this in my tri1 project. Our crossover team used a Wikipedia API.
We have all participated in code Crowdsourcing by using GitHub. Many of you have forked from the Teacher repository, or exchanged code with fellow students. Not only can we analyze GitHub code, but we can obtain profiles and history about the persons coding history. What is the biggest discovery you have found in GitHub?
- the biggest discovery I’ve found on GitHub is GitHub.dev. It allows you to look at peoples code and it’s format through the web.
Kaggle datasets for code and science exploration. The avenue of data points us youtube or netflix channels. Analyzing crowd data helps us make decisions. Exam top 10 to 20. Did you see anything interesting?
- there is a lot of medical apis, car apis, covid data, election results, and even arrests in the city of Chicago.
CompSci has 150 ish principles students. Describe a crowdsourcing idea and how you might initiate it in our environment?
- I think slack is in a sense apcsps form of crowd sourcing. Important information is sent there and people can ask questions and get answers on the slack as well
What about Del Norte crowdsourcing? Could your project be better with crowdsourcing?
- Del Norte definitely needs better crowd sourcing. Currently, a lot of decisions made by the school are done by the staff or ASB, however regular students don’t really have a chance to say much. I think making a board of students could help with this problem. These students could get feedback from classes and then give that input to those who make final decisions.
- my own project could be better with crowd sourcing because it would gain more advice and perspectives thus allowing it to grow
What kind of data could you capture at N@tM to make evening interesting? Perhaps use this data to impress Teachers during finals week.
- I could make a google form, but to make it more csp related, I could set up a SQLite database to collect feedback from every student who stops to see the project. This feedback would all be collected in one place.
5.5 Legal and Ethical Concerns
- When you create a GitHub repository it requests a license type. Review the license types in relationship to this Tech Talk and make some notes in your personal blog.
- Creative Commons Zero v1.0 Universal: The Creative Commons CC0 Public Domain Dedication waives copyright interest in a work you’ve created and dedicates it to the world-wide public domain
- Open Source GPL License: The GNU GPLv3 also lets people do almost anything they want with your project, except distributing closed source versions.
- Open Source MIT License: This allows using code freely and making and distributing closed source versions. Typically, the author of software with MIT License want credit. Credit could be as simple as adding the authors name in comments.
- In your blog, summarize the discussions and personal analysis on Software Licenses/Options, Digital Rights, and other Legal and Ethical thoughts from this College Board topic.
- There are different types of licenses, but there are open source and closed source licenses. Open source licenses force companies or individuals to have their code be public and closed source allows the code to be kept private. Some of these licenses prevent distribution of closed source versions of their work.
- Digital rights are software to protect, play, and/or distribute content. An example of digital rights are the terms of service that you often have to agree to before purchasing something. I myself, have subscriptions to things like netflix and youtube that allow me to have privileges to view or listen to different content. However, there are some ways to bypass these digital rights such as through illegal websites.
- in terms of ethics, there are some issues. Many people want to bypass digital rights through illegal website but by doing this the artists and owners of the content don’t get paid for their work, instead people can view it for free. This can have a negative impact on the income of those people.
- Make a license for your personal (blog) and Team repositories for the CPT project. Be sure to have a license for both Team GitHub repositories (frontend/backend). Document license(s) you picked and why. FYI, frontend, since it is built on GitHub pages may come with a license and restrictions. Document in blog how team made license choice and process of update.
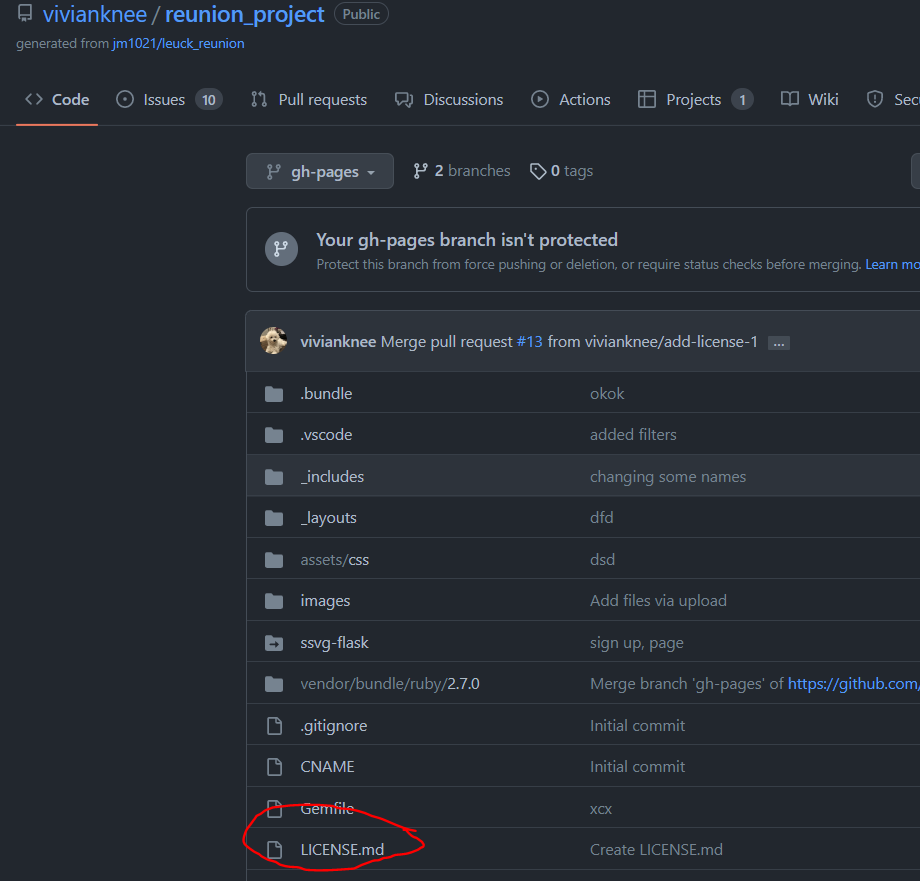
- Fast Pages Blog: I added a license file called LICENSE.md. I added a GNU General Public License v.3.0
- I did the same thing for our teams backend and frontend servers
- Fast Pages Blog: I added a license file called LICENSE.md. I added a GNU General Public License v.3.0
5.6 Safe Computing
- Describe PII you have seen on project in CompSci Principles.
- In our project, we have a user login and sign-up system which requires the users email as well as a password of their choice. Both these these are considered PII
- What are your feelings about PII and your personal exposure?
- I believe that some PII will inevitably be out there for everyone to see but it’s crucial that more risky information like passwords and personal credentials stay to oneself. I have PII that I put on the internet. Specifically, I use instagram and linkedin where I have my name, accomplishments, etc. listed.
- Describe good and bad passwords? What is another step that is used to assist in authentication.
- a bad password is one that has no system of authentication. For example, Symmetric encryption is not a good system for passwords as it is a type of encryption where only one key (a secret key) is used to both encrypt and decrypt electronic information. A good password has a system of authentication. For example, good passwords use Multi-factor authentication which often requires you to enter a code that has been texted or emailed to you. Another good method to have a good password with good authentication is Asymmetric cryptography. Asymmetric cryptography, also known as public-key cryptography, is a process that uses a pair of related keys – one public key and one private key – to encrypt and decrypt a message and protect it from unauthorized access or use.
- Try to describe Symmetric and Asymmetric encryption.
- Symmetric encryption is not a good system for passwords as it is a type of encryption where only one key (a secret key) is used to both encrypt and decrypt electronic information.
- Asymmetric cryptography, also known as public-key cryptography, is a process that uses a pair of related keys – one public key and one private key – to encrypt and decrypt a message and protect it from unauthorized access or use. We did this for the security of our fastpages site, using a public and private key
- Provide an example of encryption we used in AWS deployment.
- Describe a phishing scheme you have learned about the hard way. Describe some other phishing techniques.
- sometimes I will get dms from my friends on discord with a link to “free nitro” but in reality the link gets you to fil out personal information which it then uses to hack your discord account. Unfortunately, Ive had this happen to me on discord and Instagram.