CollegeBoard TRI 2 MC Final Notes
- Takeaways
- Questions
- Q50: A computer scientist is analyzing four different algorithms used to sort a list. The table below shows the number of steps each algorithm took to sort lists of different sizes. Based on the values in the table, which of the algorithms appear to run in reasonable time?
- Q49: A city planner is using simulation software to study crowd flow out of a large arena after an event has ended. The arena is located in an urban city. Which of the following best describes a limitation of using a simulation for this purpose?
- Q43: What is displayed as a result of the procedure call proc2(“birthday”, “to you”) ?
- Q17: Both online newspapers and social media sites are used to distribute information on the Internet. Which of the following best describes an advantage that online newspapers have over social media sites?
- Q13: An author is considering publishing an e-book using a Creative Commons license. In which of the following situations would it be better for the author to use a Creative Commons license instead of a traditional copyright?
- Q2: Which of the following has the greatest potential for compromising a user’s personal privacy?
Takeaways
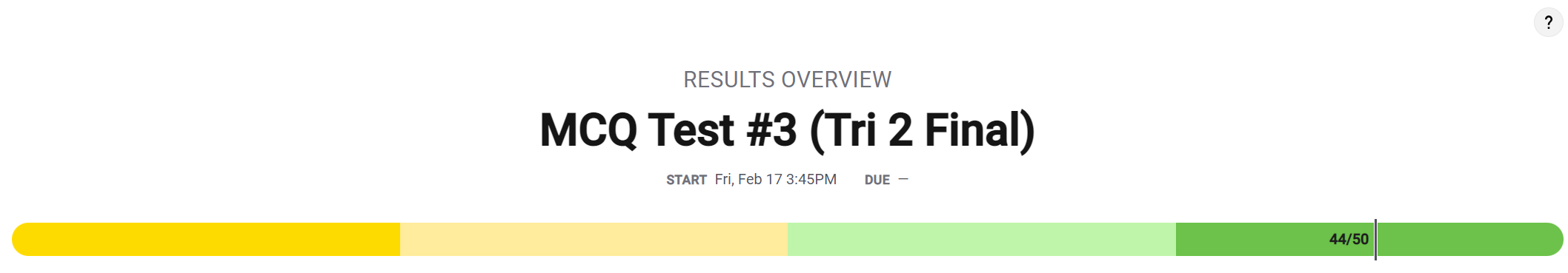
- On my collegeboard MC #2, my score was 44/50
- The topics of questions I got wrong included
- Algorithmic Efficiency
- Simulations
- Calling Procedures
- Beneficial and Harmful Effects
- Legal and Ethical Concerns
- Safe Computing
Questions
Q50: A computer scientist is analyzing four different algorithms used to sort a list. The table below shows the number of steps each algorithm took to sort lists of different sizes. Based on the values in the table, which of the algorithms appear to run in reasonable time?
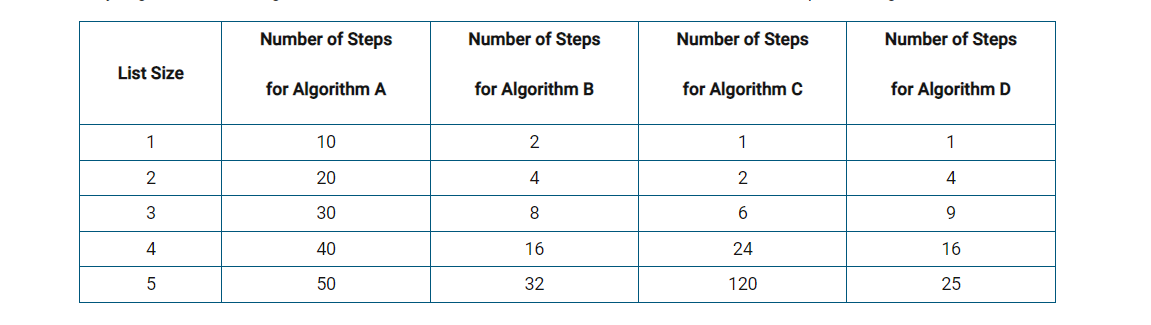
- I chose B and C when it was actually A and D
- Notes
- I think I just didn’t understand what this question was asking me to do.
- The reason the answer is neither B or C is because as the size of the list grows the number of steps required to sort them grows at an exponential rate and factorial rate respectively. This indicates that the algorithm does not run in reasonable time.
- A and D are the answers because they increase at a rate that is reasonable as the list grows in size
Q49: A city planner is using simulation software to study crowd flow out of a large arena after an event has ended. The arena is located in an urban city. Which of the following best describes a limitation of using a simulation for this purpose?
-
I chose: “The model used by the simulation software cannot be modified once the simulation has been used.” but the answer was “The model used by the simulation software often omits details so that it is easier to implement.”
-
Notes
- The model used by a simulation can be modified, both before and after running the simulation. In fact, one of the benefits of using a simulation is the ease of modification.
- Simulations are limited by the model that is used. There may be many reasons for using a simplified model, including ease of implementation. Thus B was the answer
Q43: What is displayed as a result of the procedure call proc2(“birthday”, “to you”) ?
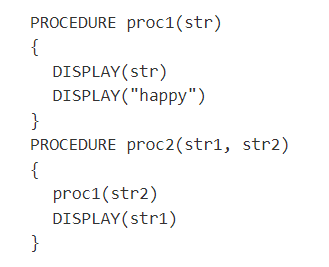
- I chose “to you birthday happy” but the answer was “to you happy birthday”
- Notes
- In proc2, the call to proc1 occurs before the DISPLAY statement, so “to you” and “happy” are displayed before “birthday”.
Q17: Both online newspapers and social media sites are used to distribute information on the Internet. Which of the following best describes an advantage that online newspapers have over social media sites?
- I chose the answer that said “The ability to provide information that is widely accessible” but the correct answer was “The ability to provide credibility to the information distributed”
- Notes
- my answer choice doesn’t make total sense because not everyone has access to the internet or a device so online newspapers are in fact not accessible to everyone. This was something that we covered in the digital divide unit.
- Online newspapers are usually run out in the open, in that the people who create the newspaper are clearly noted on the website. In addition, these online newspapers are often connected to physical newspapers, which are considered credible sources of information.
Q13: An author is considering publishing an e-book using a Creative Commons license. In which of the following situations would it be better for the author to use a Creative Commons license instead of a traditional copyright?
- The author wants to make the e-book available as a free download.
- The author wants to prevent people from sharing copies of the e-book on peer-to-peer networks.
- The author wants to allow people permission to use and modify the e-book.
- I said 1 only but the answer was 1 and 3
- Notes
- Statement I is correct because the Creative Commons license is designed to increase the amount of content available to the public for free.
- Statement III is correct because under Creative Commons the author can stipulate what kind of modification is allowed by users.
- I need to review what licenses allow people to do
Q2: Which of the following has the greatest potential for compromising a user’s personal privacy?
- I chose “The Internet Protocol (IP) address of the user’s computer”
- The correct answer was “A group of cookies stored by the user’s Web browser”
- Notes
- The aggregation of information in browser cookies can be used by websites that the user visits to track the user and collect information about the user. This is why they are potential concerns for a user’s privacy
- The IP address of a user’s computer is required for the user to send and receive information on the Internet. The IP address in itself does not contain any extra information about the user. However, isn’t it true that an IP address can reveal information on where your exact location is? Or is there security to prevent this?